Dimension Data has released the findings from its Network Barometer Report 2011, now in its third year.
The Report is based on actual metrics from electronic collection, and not from a survey.
The key findings cover network device vulnerabilities and configuration issues, lifecycle status and operating systems in use.
The data in the Report has been aggregated from 270 Technology Lifecycle Management (TLM) Assessments conducted during the 2010 calendar year, including 22 TLM Assessments completed on Australian organisations. Dimension Data’s TLM Assessment is an IT infrastructure asset assessment that discovers installed assets on the organisation’s network, identifying their lifecycle status, configuration and maintenance coverage. The TLM Assessment covers multiple networking vendors, but the networks assessed were predominantly Cisco-based.
The full Network Barometer Report 2011 is available on request.
Gregg Sultana, Dimension Data’s National Network Integration Manager, provides some additional commentary on the press releases, and is also available for further comment in relation to the Network Barometer Report:
“In terms of vulnerabilities uncovered, the prevalence of a specific security vulnerability (PSIRT* 109444) can be explained in part due to the particular vulnerability existing across a wide range of networking devices, and in part due to strategies that organisations adopt to mitigate the risk, such as employing specific configuration workarounds to negate the vulnerability.”
“We found on average 9.3 configuration policy violations per device for AAA authentication configurations – which is very worrying, because this relates directly to the control of configuration access to network devices. Access control is fundamental to network security and, if managed poorly, undermines any other configuration and vulnerability management practices in place in the organisation.”
“In our 2010 data, we found on average 28 unique versions of IOS (network device operating software) running across networking devices in each organisation – with 11 running in excess of 100. While it’s normal to run different IOS versions across different parts of the network (i.e. due to different platforms), there is no optimal number to run, its definitely good practice to be standardising as much as possible in each specific platform or class of networking device.
“Since 2009 we have been running TLM Assessments with clients and collating data into the Network Barometer Report. From a lifecycle perspective we have seen that organisations are getting smarter around understanding and managing the lifecycle of their networking devices. More organisations are now no longer waiting until the LDoS (Last Day of Support) milestone before they retire the devices. They are adopting a more strategic approach and managing to earlier milestones such as EoCR (End of Contract Renewal) or EoSWM (End of software Maintenance).”
* A PSIRT is a software vulnerability that has been identified by Cisco’s Product Security Incident Response Team. Each PSIRT identifies a unique IOS vulnerability based on extensive lab testing and research by Cisco.
MEDIA RELEASE
ORGANISATIONS WORLDWIDE NOT KEEPING UP WITH NEW SECURITY THREATS
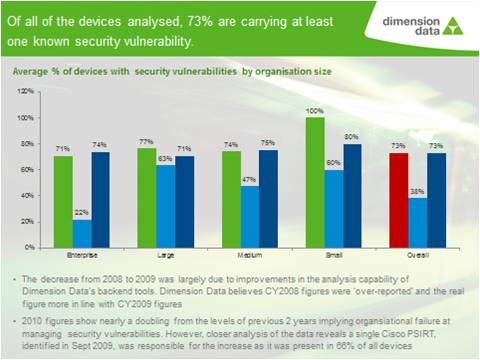
73% of network devices analysed by Dimension Data carry at least one known security vulnerability
Over 73% of corporate network devices analysed by Dimension Data during 2010 were carrying at least one known security vulnerability. This is almost double the 38% recorded in 2009. The data also revealed that a single higher risk vulnerability - PSIRT 109444** – which was identified by Cisco in September 2009, was found in a staggering 66% of all devices, and was responsible for this jump.
These are some of the key findings in the Network Barometer Report 2011 published today by the global specialist IT services and solutions provider. The Report covers aggregate data compiled from 270 Technology Lifecycle Management (TLM) Assessments conducted in 2010 worldwide by the Group for organisations of all sizes across all industry sectors. It reviews the networks’ readiness to support business by evaluating the configuration variance from best practices, potential security vulnerabilities, and end-of-life status of those network devices.
“Given the pressure that organisations are under from regulatory bodies, consumers and their executive to protect customer information and privacy, as well as sensitive business
information from both cyber criminals and competitors, it’s hard to believe that they would knowingly expose themselves to this level of risk”, says Neil Campbell. “The truth of the matter is that many organisations still don’t have consistent and complete visibility of their technology estates. In fact, previous research not related to the Network Barometer Report carried out by Dimension Data found that clients are unaware of as much as 25% of their networking devices.”
But it’s not all bad news. While discovery processes may be falling short of the market, Campbell said that apart from the one security vulnerability on 66% of devices, organisations are trying to up their game with regards to remediation. According to the Report, the TLM Assessment results showed that if PSIRT 109444 was taken out of the equation, organisations had patched fairly well: the next four vulnerabilities were found in less than 20% of all devices.
**A PSIRT is a software vulnerability that has been identified by Cisco’s Product Security Incident Response Team. Each PSIRT identifies a unique IOS vulnerability based on extensive lab testing and research by Cisco.
However, as the prevalence of PSIRT 109444 illustrates, a pervasive threat can occur literally overnight. “It only takes one vulnerability to expose the entire organisation to a security breach, so organisations must do much more if they want to adequately protect themselves,” says Campbell. “This includes increasing the number of regular network scans to ensure that any vulnerability is picked up before it causes serious business continuity, compliance failure, or reputational damage.”
Could just one security vulnerability really put an organisation at this level of risk? “Absolutely,” Campbell says. “To a hacker, a security vulnerability is equivalent to leaving one’s front door unlocked. And attempting to exploit vulnerabilities is usually the first port of call when initiating an attack. That’s because it may provide the hacker with full access to the device, which he could use as a launch pad to initiate further attacks internally.
“Organisations which are not ahead of the game when it comes to knowing and protecting themselves against the latest threats are playing a Russian Roulette of risk, and could be looking at a medium- to high-risk security threat like PSIRT 109444, and be at risk of a security vulnerability that falls into the extreme - or even critical - category.”
Other significant findings in the Report include:
- the percentage of network devices past last-day-of-support has dropped dramatically from 31% last year to 9% in the 2011 results;
- the percentage of devices past end-of-sale which are in ‘late stage’ end-of-life sits at 47%, but there‘s some evidence that organisations are more aware of where to draw the line when it comes to risk.
To download the Network Barometer Report 2011, please visit www.dimensiondata.com/networkbarometer
-ENDS-
About Dimension Data
Founded in 1983, Dimension Data plc is an ICT services and solutions provider that uses its technology expertise, global service delivery capability, and entrepreneurial spirit to accelerate the business ambitions of its clients. Dimension Data is a member of the NTT Group. www.dimensiondata.com
